Just a little bit of extra knowledge and experience makes all the difference in the world of Incident Response. With over 500,000 open cybersecurity positions in the US alone according to CyberSeek and over 4 Million open positions globally according to (ISC)2, Incident Response team members have the responsibility to ensure they have as much knowledge and experience as possible. Additionally, with malicious threat actors having the element of surprise, understanding how to discover attacker behavior becomes even more important.
Thus, we are excited and proud to introduce you to our new series: The MITRE ATT&CK Enterprise Framework Collection video series. For those who are not already familiar, MITRE ATT&CK is a collection of attacker behaviors displayed across the Cyber Attack Lifecycle. MITRE and the contributing cybersecurity members involved have taken thousands of known attacks, analyzed all attacker behaviors involved, and created what is now three separate frameworks: MITRE PRE-ATT&CK, MITRE ATT&CK Enterprise, and ATT&CK for Mobile.
- MITRE PRE-ATT&CK: Focuses on all the behaviors attackers exhibit during the recon and weaponization stages of the Cyber Attack Lifecycle (formerly known as the Cyber Kill Chain articulated by Lockheed Martin.)
- MITRE ATT&CK Enterprise: Tightly coupled to enterprise-specific network types, (Microsoft Windows, Linux, etc.). ATT&CK Enterprise focuses on the next five phases of the Cyber Attack Lifecycle with detailed technical information relative to adversary actions and defender mitigations for each technique.
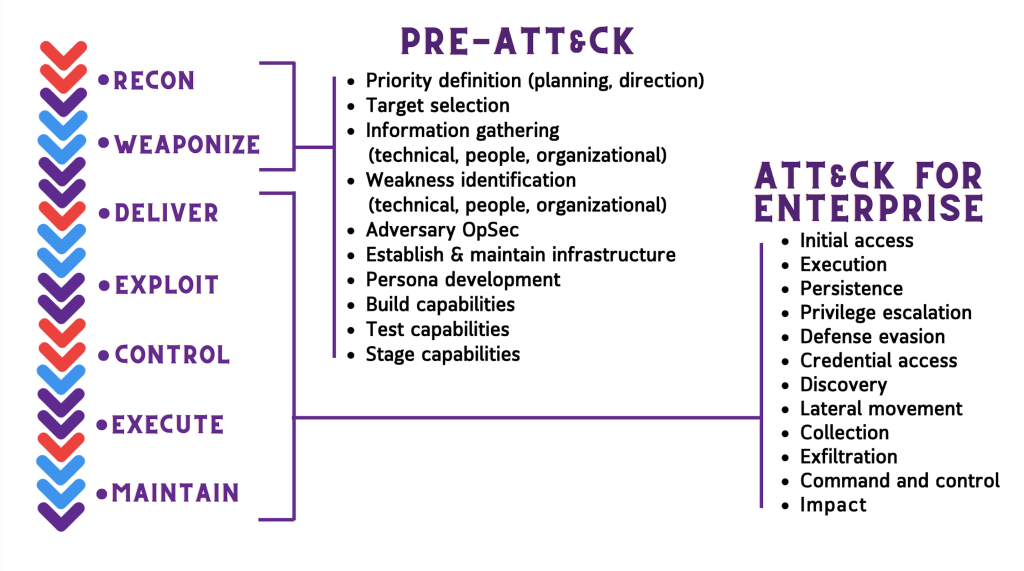
- ATT&CK for Mobile: Built upon NIST’s Mobile Threat Catalogue and provides a model of adversarial tactics and techniques used to gain access to mobile devices and take advantage of that access to accomplish adversarial objectives.
At Cyberbit, we have chosen to focus our first video series on MITRE on MITRE ATT&CK Enterprise to provide enterprise SOC team members with a new perspective on MITRE. Most of the focus until now has been on the attacker’s behaviors and actions. For the first time, we are presenting MITRE ATT&CK for Enterprise from the defender’s point of view!
Over the course of the video series, we will provide examples of MITRE ATT&CK Enterprise Tactics, Techniques, and Sub-Techniques from the point of view of analysts on the Incident Response team. We can record these videos as if there is an attack in progress due to the power of Cyberbit Range. Using various versions of the real-world attacks included in Cyberbit Range, we have recorded examples of various techniques included in MITRE ATT&CK Enterprise. Each video will focus on one tactic, providing two or three examples of techniques included in the category. For example, in our Collection video, we focus on Input Capture, Email Collection, and Automated Collection.
The goal of these videos is to help members of the Incident Response team learn to recognize the various techniques included in each tactic. By watching each short video, you will gain valuable information that will help you to perform better in your role on a daily basis. Over the next few months, we will continue to deliver new videos, giving you a sneak peak of MITRE ATT&CK Tactics and Techniques to help you continually improve, whether it be through education or hands-on training!

