The recent Triton ICS malware attack is a custom-tailored ICS malware that also earned the moniker “TRISIS” because it targets a vulnerability in Schneider Electric’s EcoStruxure™ Triconex Safety Systems safety instrumented system (SIS) that enables the malware to replace the logic in PLCs that send commands directly to physical machinery. the Triton ICS malware is the fifth known malware that specifically targets ICS/SCADA networks and as of publication, has carried out at least one successful attack against a plant in the Middle East.
Triton ICS Malware Incident Summary
Triton ICS malware acts as a payload after hackers have already gained deep access to a facility’s network. When Triton is installed in an industrial control system, the code scans for Schneider’s Triconex equipment, confirms that it can connect to it, and then begins injecting new commands into its operations. If the malware’s malicious commands aren’t accepted by the Triconex components, it can crash the Triconex safety system.
The hackers deployed Triton on a Windows-based engineering workstation. The malware leaves legitimate programs running on the controllers in place, but adds its own programs to the execution table. In case of failure, the malware attempts to return the controller to a running state or overwrite the malicious program with junk data, likely in an effort to cover its tracks.
Triton ICS Malware Puts People and Production at Risk
Once the SIS controller has been compromised, the attacker can reprogram the Triconex device to trigger a safe state, which could cause downtime and result in financial losses. Attackers could also reprogram the SIS so that it allows dangerous parameters without triggering the safe state, which can have a physical impact, potentially people in the plant in addition to production and equipment.
Since Triconex systems are designed to “fail-safe,” that would lead to other systems turning off as a safety measure, disrupting a plant’s operations. If the safety system fails, all other systems grind to a halt.
4 ways to protect against Triton (TRISIS) ICS Malware
Network administrators should review the IP addresses, domain names, file hashes, network signatures, and YARA rules provided and add the IPs to their watchlist to determine if any malicious activity has occurred within their organization. System owners are also advised to run the YARA tool on any system suspected to have been targeted by these APT actors.
Switch key procedures – Implement change management procedures for changes to key position. Audit current key state regularly.
Switch key position – Leverage hardware features that provide for physical control of the ability to program safety controllers. These usually take the form of switches controlled by a physical key. On Triconex controllers, keys should not be left in the PROGRAM mode other than during scheduled programming events.
ICS traffic – Monitor ICS network traffic for unexpected communication flows and other anomalous activity.
TCP/IP endpoints – Implement strict access control and application whitelisting on any server or workstation endpoints that can reach the SIS system over TCP/IP.
* Triconex customers should follow vendor updates on the Schneider Electric Cybersecurity Support Portal
Why Cyberbit SCADAShield customers are safe
Cyberbit provides the SCADAShield OT security solution which uses several techniques to detct ICS/SCADA malware attacks like Triton:
Continuous monitoring and policy enforcement – Granular DPI, continuous OT scanning and policy-building mechanisms ensure that the customer’s OT environment is under constant supervision to ensure maximum detection and organizational policy enforcement.
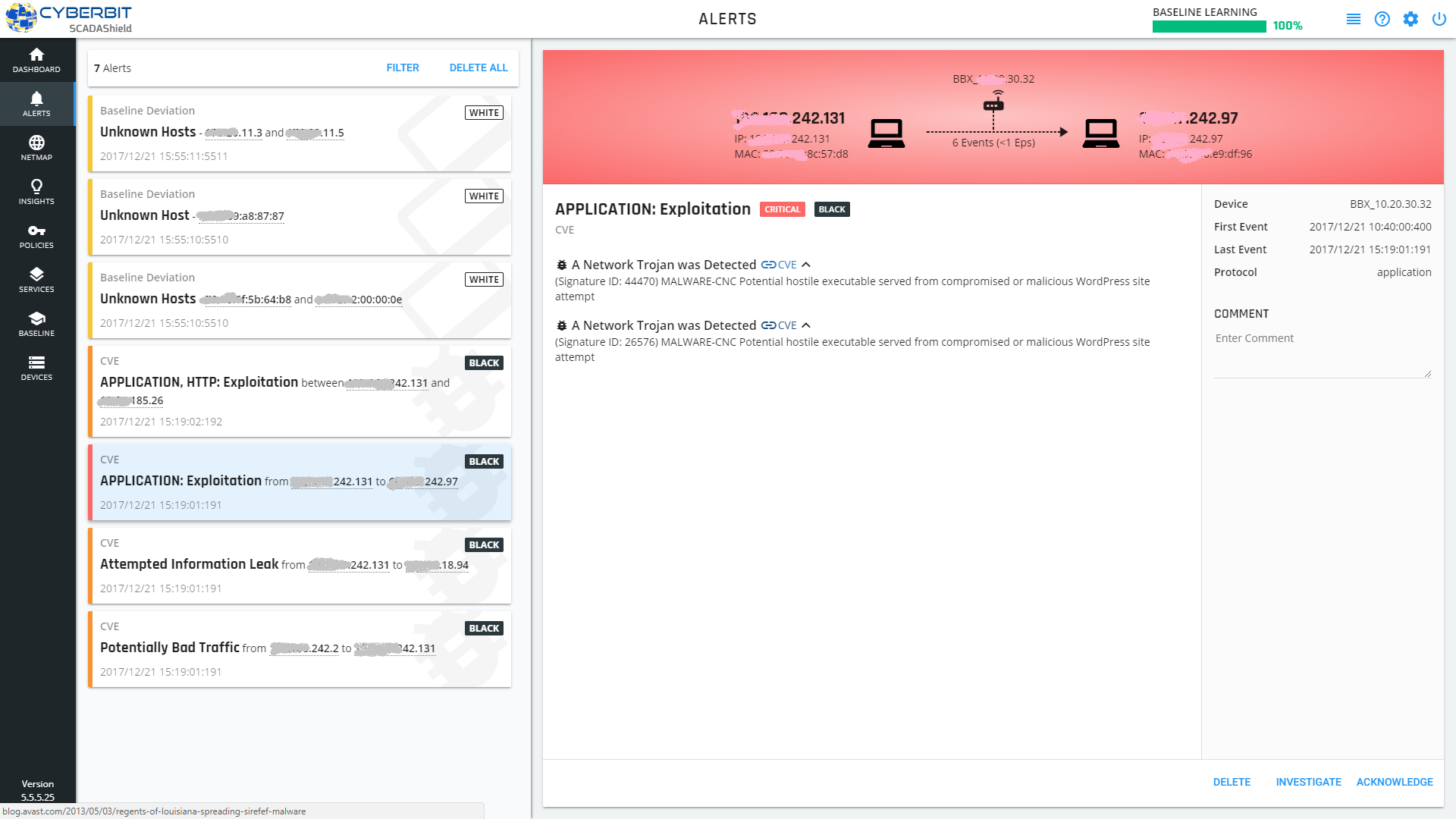
Continuous alert aggregation and reasoning mechanism – Continuous scanning and alert aggregation and alert reasoning Mechanism ensure that security regulations are continuously been kept and enforced. In the event a breach occurs, it can be handled and fixed very quickly, keeping downtime to an absolute minimum. SCADAShied Alert Reasoning and Alert Aggregation dashboards give OT managers visibility by:
• Quickly and directly pinpointing OT vulnerabilities to enable a fast response.
• Explaining the rationale behind the alert (black policy or VCE violation, detection of new hosts, connection, protocol or command)
Alert Reasoning and Alert Aggregation dashboard – Cyberbit SCADAShield
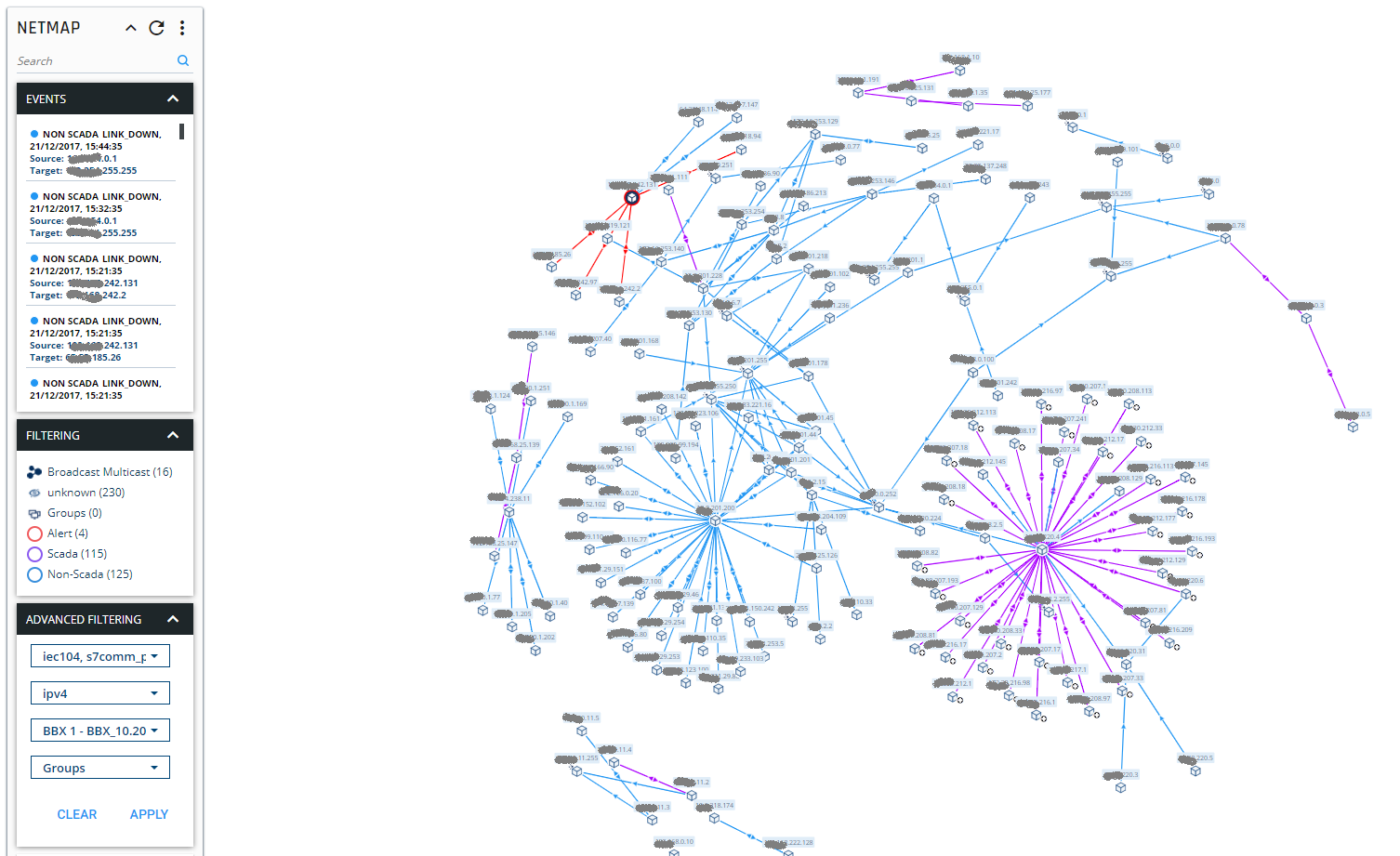
Clear mapping of critical zones – SCADAShield’s NetMap Grouping feature assures that the organization’s most critical and vulnerable zones are dynamically mapped, making it easy to closely monitor and control day-to-day activity. The OT manager can see where exactly an attacked happened, which assets are under attack, the communication protocols and which additional assets may also be at risk.
SCADAShield NetMap
Download ENCS Report Executive Summary
Ronen Rabinovich is ICS/SCADA Security Product Manager at Cyberbit.

