The most feared part of the upcoming EU General Data Protection Regulation is the steep GDPR fines. The new regulation will take full effect in May 2018 and is relevant to all companies – whether they’re located in the EU or not – that collect, store or process personal data of EU residents. The regulations have two main parts:
- usage and security of private data
- breach response actions
The main difference between the two parts is that the first one, data usage regulation, is a complex task that can be handled based on structured methodologies and calculated risk assessment. Contrarily, the second part is mainly focused on the breach notification rule which requires notifying the official EU authorities and people whose personal data could potentially be affected by the breach within 72 hours. The notification requirement will need to be met during a crisis. This means the entire organization will be under severe pressure and have to deal simultaneously with conflicting requirements such as; technological, business, legal, public relations, insurance and, last but not least, meeting the regulatory requirements to avoid paying GDPR fines.
Correctly responding to all these aspects of a major cyber breach including data exposure requires four main ingredients:
Methodology – The first step to prepare to handle cyber incidents is defining the organizational methodology; the organizational policies and practices which support the decision-making process for handling the various aspects of the incident. The incident response methodology covers all the technological, business and legal considerations, including;
- classification of incidents
- definition of the functions in the organization which must be part of the decision process for each incident class
- definition of priorities for activities for each kind of incident
- definitions of workflows and data flow for incident types
- do’s and don’ts for specific scenarios
Only solid methodology and preparation will ensure that the right actions will be taken in the right order, and minimize the potential for mistakes. Errors in incident response methodology can damage the ability to investigate and analyze the event. This reduces the potential for proper recovery and exposes the organization to legal and business risks. Therefore the organizational and technical incident handing methodology should be detailed enough to cover a wide variety of incident types and scenarios.
Visibility – Correct decision-making during a cyber incident requires deep and wide visibility to understand the nature and the scope of the breach quickly. Analysts need to identify the attack process, the complete and accurate impact of a breach, and the data exposure. Visibility must enable correlation between the incident information and other organizational factors that can dictate the response actions.
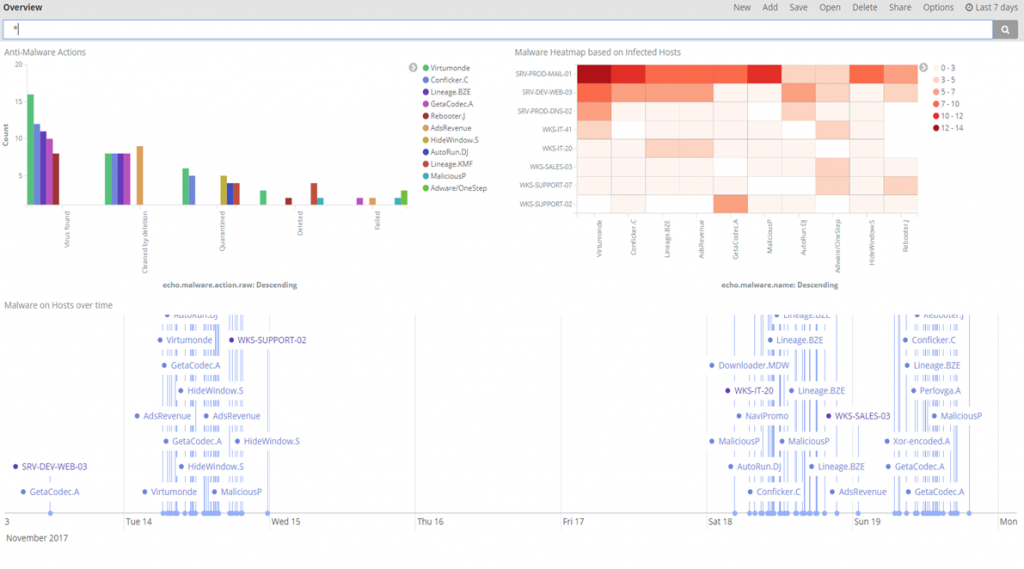
Malware Overview Dashboard – SOC 3D
Tools – To achieve compliance and prevent paying GDPR fines, an organization must implement a set of technologies to enable implementation of the methodology and grant the visibility needed to analyze the situation, collect all relevant data and coordinate and communicate with all the relevant decision-makers in the organization according to the methodology.
This requires a toolset that covers all stages of incident handling; from detection and analysis to carrying out the full response. Orchestration tools are of utmost importance to ensure the methodologies are carried out precisely.
Training – Methodology and tools provide limited effect without trained personnel that will know how to use the tools to follow the methodology. Personnel must have the opportunity to practice carrying out incident response methodologies in realistic conditions. Every member of the organization gains experience carrying out their part of the response and fully understands their role and responsibilities. Realistic practice is the most effective way to prepare teams to respond to the ‘real thing’. It also gives team members and executive management the confidence that they are prepared to deal with all incidents, including nightmare mega-breach scenarios and will be able to meet the GDPR requirements for notification. The best way to avoid the steep GDPR sanctions is to develop and practice operating real breach scenarios.
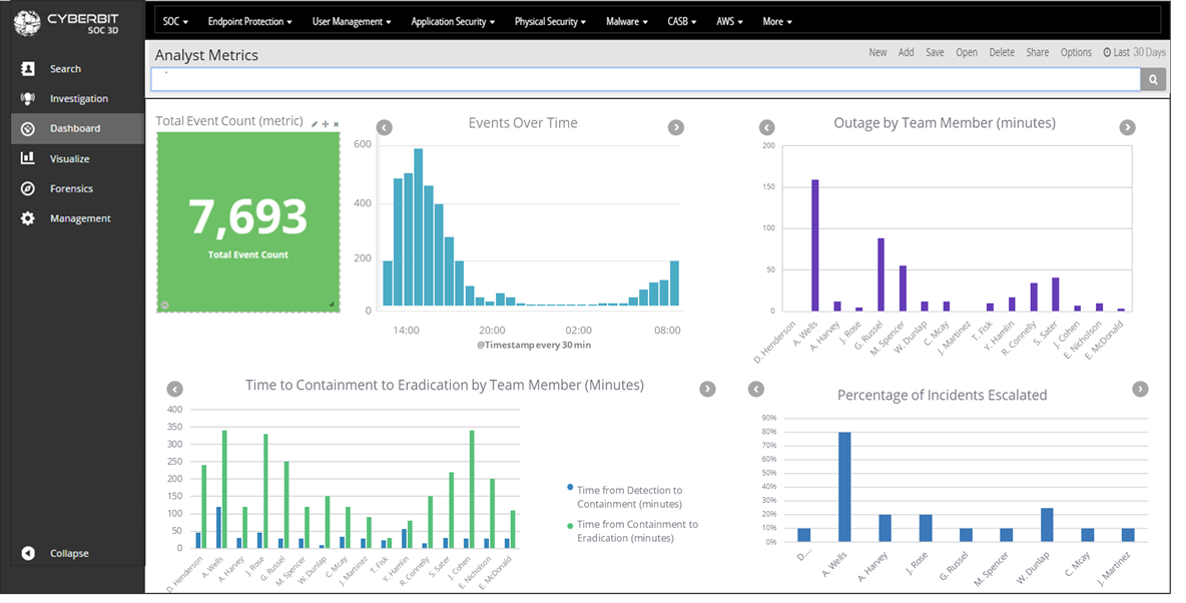
Analyst Performance Measures – SOC3D
Can GDPR Fines be Avoided by Outsourcing?
Some organizations outsource their security operations to a specialized manager security service provider (MSSP). This approach has pros and cons but in some cases, it is the only relevant option. When evaluating if an MSSP is the best solution for your organization, it is important to take into consideration several aspects and how it will impact your overall cybersecurity and evaluate the ability to be compliant with GDPR. Ultimately, the decision must be made on a thorough assessment of which option will get you compliant and guarantee you won’t have to incur the additional cost of GDPR fines.
A security service provider brings considerable expertise, advanced toolset and robust staffing capabilities to handle many aspects of cybersecurity and breaches. Nevertheless, it is impossible to outsource all incident response responsibilities. For example, in most cases, the MSSP can’t handle the business, legal and public relations aspects. If you are considering engaging an MSSP, you must begin by analyzing the gaps between the organizational methodology and the proposed services and then define integrated policies and practices. Detailed workflows must be developed that focus specifically on the seams between responsibilities of the service provider and the organization.
Compliance with the GDPR notification regulation will require enterprises to dramatically shorten the time it takes to notify authorities and affected customers about a breach. Currently, this can take weeks, even months, but now organizations will be required to issue notifications within just 72 hours, or face heavy GDPR fines. This tight notification timeline will be very difficult to meet and create a lot of pressure on security managers and teams. The threat of fines may cause organizations to ‘err on the side of caution’ and quickly release breach notifications before they have a fully understood the breadth of the damage. News of a breach is bad enough, but inaccurate announcements can strike a further blow to reputation by making the impression the security operations are not capable of fully understanding what has happened and how to respond. To avoid potential losses from GDPR fines and reputation damage, organizations must develop and deploy a strict methodology, supported by the right tools that provide visibility and decision support to meet the notification requirements.
Download FREE: 5 Ways of Empowering Incident Response
Ami Braun is VP Business Development at Cyberbit.

